How to Create and Manage User Accounts in Active Directory

Active Directory (AD) remains the primary identity management platform in Windows-based enterprise environments.
At its core, it manages user authentication, authorization, and provisioning across a domain. User accounts serve as the operational link between individuals and the IT resources they access, such as files, email, devices, and applications.
Effective control of these accounts reduces privilege sprawl, enforces policy compliance, and supports business continuity.
Creating and managing users in AD is not limited to clicking through a GUI.
You'll use the Active Directory Users and Computers (ADUC) tool, PowerShell cmdlets such as New-ADUser, and, sometimes, Group Policy or Lightweight Directory Access Protocol (LDAP) interfaces.
If you're managing hundreds of users across multiple organizational units (OUs), precision becomes non-negotiable.
Understanding Active Directory User Accounts
In Active Directory, a user account is a directory object that represents a digital identity. It exists within the domain's schema and links an individual to network resources.
Each user account is defined by a collection of attributes stored in the directory database. These attributes are assigned a distinguished name (DN) and are indexed for querying through tools such as LDAP or PowerShell.
Key identifiers include the sAMAccountName (used for legacy compatibility), the UserPrincipalName (UPN, which looks like an email address), and the SID (Security Identifier, unique per user).
On top of that, attributes like CN (Common Name), displayName, and description often support administrative functions or HR integration.
You’ll find these values directly editable within ADUC or scriptable via command-line tools.
Accounts in AD fall into several categories. Standard user accounts are created for employees, contractors, or consultants.
Service accounts support applications, backups, or domain-linked automation.
Built-in accounts, such as Administrator and Guest, are created during domain setup and should be carefully controlled.
If you’ve ever wondered why a locked-down account still triggers login activity, it's probably a service account running in the background.
Tools for Managing AD Users
Graphical Interface: Active Directory Users and Computers (ADUC)
ADUC is the primary GUI for account management in domain environments. Installed via the RSAT package, it allows administrators to create, move, disable, and reset user accounts.
You can also view object properties, assign group memberships, and delegate permissions. It’s intuitive, but not ideal for bulk operations or scriptable automation.
Command-line Utilities: PowerShell and Directory Service Tools
PowerShell provides granular control over user accounts. With cmdlets like New-ADUser, Set-ADUser, and Unlock-ADAccount, you can automate repetitive tasks and manage accounts in bulk.
PowerShell supports CSV imports, conditional logic, and role-based access through scripts.
In older environments, command-line tools such as dsadd, dsmod, and dsquery remain available, though their use has declined.
You’ll appreciate how easily PowerShell integrates with scheduled tasks or compliance audits.
Group Policy Integration
While Group Policy does not create users, it allows enforcing user-level settings across the domain.
You can manage logon scripts, desktop restrictions, password policies, and environment variables based on user objects.
These policies are applied via GPMC and processed at logon. If you’ve configured password complexity without scripting anything, Group Policy did the work.
Creating a New User Account in Active Directory
Using Active Directory Users and Computers (ADUC)
To create a user account using ADUC, open the console and navigate to the target Organizational Unit (OU). Right-click the OU, select New, then choose User. Enter the full name and user logon name (UPN), then proceed to set the password.
Check the options for password behaviour: User must change password at next logon or Password never expires. You can also deactivate the account until activation is ready. After saving, the new object appears under the selected OU, inheriting its delegated permissions and policies.
It’s best practice to assign group memberships immediately and verify the account’s replication across domain controllers.
Using PowerShell (New-ADUser Command)
The PowerShell equivalent offers greater control and automation. Launch an elevated PowerShell session with the ActiveDirectory module loaded. Use the New-ADUser cmdlet to define attributes.
A basic command looks like this:
New-ADUser -Name "Ayo Mbabazi" -GivenName "Ayo" -Surname "Mbabazi" -SamAccountName "ambabazi" -UserPrincipalName "ambabazi@domain.local" -Path "OU=Staff,DC=domain,DC=local" -AccountPassword (Read-Host -AsSecureString "Enter Password") -Enabled $true
You must specify an OU path, account status, and initial password. Additional switches configure profile paths, expiry, logon hours, or user scripts.
Besides being scriptable, PowerShell ensures exact attribute control.
Modifying Existing User Accounts
Edit User Attributes
In ADUC, right-click the user object and select Properties. From there, you can edit fields like job title, department, email, phone number, and manager. Changes are updated immediately within the directory.
PowerShell provides deeper control. Use Set-ADUser with attribute flags:
 Besides being faster, PowerShell avoids GUI field defaults that sometimes overwrite manually set properties.
Besides being faster, PowerShell avoids GUI field defaults that sometimes overwrite manually set properties.
Reset Passwords
To reset a user’s password via ADUC, right-click the account, choose Reset Password, and enter the new credentials. You can enforce a password change on the next logon from the same dialog.
With PowerShell, use:
Set-ADAccountPassword -Identity "ambabazi" -NewPassword (ConvertTo-SecureString "P@ssw0rd2025" -AsPlainText -Force)
On top of that, you can combine this with Enable-ADAccount to re-enable users after a reset.
Unlock User Accounts
In ADUC, go to the user properties under Account, then check the Unlock Account box. This appears only if the account is locked by policy.
PowerShell provides a faster method:
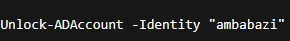 You’ll find this especially useful in environments with lockout thresholds and remote support tickets. (And yes, it works even when the GUI doesn’t load.)
You’ll find this especially useful in environments with lockout thresholds and remote support tickets. (And yes, it works even when the GUI doesn’t load.)
Move Users Between Organizational Units
Right-click the user object in ADUC and select Move. Choose the new OU from the list. This preserves all user attributes, including group memberships and SID.
In PowerShell, use:
Move-ADObject -Identity "CN=ambabazi,OU=Staff,DC=domain,DC=local" -TargetPath "OU=Projects,DC=domain,DC=local"
Keep in mind, replication delays may affect visibility across domain controllers.
Disabling, Deleting, and Restoring Accounts
Disabling User Accounts
Deactivating an account blocks logon access without removing the user object. Use it when employees are on leave, suspended, or being offboarded in phases.
In ADUC, right-click the user and choose Disable Account. A down arrow appears on the icon. To reverse, right-click and select Enable Account.
PowerShell provides more flexibility:
Disable-ADAccount -Identity "ambabazi"
This command runs instantly and can be used in scripts managing inactive users.
Deleting User Accounts
Deleting removes the object from the directory and severs all associations—group memberships, SIDs, profile links. Use this when the user will not return.
In ADUC, select the user, press Delete, and confirm. You’ll need administrative permissions for this action.
PowerShell command:
Remove-ADUser -Identity "ambabazi"
Remember to document or archive critical attributes before deletion. (You’ll thank yourself later if that user ran automated scripts.)
Restoring Deleted Accounts
If the AD Recycle Bin feature is enabled, you can recover deleted users along with most metadata. Restoration is time-sensitive—deleted objects have a default tombstone lifetime.
ADUC doesn’t support object recovery. Use PowerShell:
Get-ADObject -Filter 'Name -like "*ambabazi*"' -IncludeDeletedObjects | Restore-ADObject
You must run this from a domain controller or from an elevated PowerShell session with access to the deleted objects container.
Conclusion
Account provisioning and lifecycle management in Active Directory shape every authenticated interaction in your domain.
Each user object represents an operational checkpoint, whether for access, identity, or security. Besides technical accuracy, the task demands repeatability and awareness of long-term directory behaviour.
On top of that, changes made today may influence audit trails, compliance reports, or recovery decisions months later.
If you're responsible for managing these users, treat each operation as deliberate. The system does exactly what it's told, and usually nothing more. That’s part of the job.
Read also: How to Recover Deleted Files in Windows 10
